What Is Smart Contract Verification and Why It Matters
Learn what smart contract verification is, how it works, and why it matters for blockchain security. Understand verified vs unverified contracts and how to stay safe

When you interact with a smart contract on a blockchain, you're relying on the underlying code to transact your valuable assets, send your data, or complete complex transactions.
But how can you trust that this code will handle your transactions securely? For starters you can read the code and see how it works. This is where smart contract verification becomes critical for blockchain security.
Smart contract verification is the process of proving that the code you see matches the code running on the blockchain. Without it, you're essentially sending funds or data to a black box with no way to confirm what happens next.
Understanding the Basics: Source Code vs Bytecode
Developers (or increasingly AI agents 🤖) write contracts in human-readable programming languages like Solidity or Vyper. This is the source code that people can read, review, and audit.
But blockchains don't run source code directly. Before deployment, the code gets compiled into bytecode, which is a long string of hexadecimal characters (0x6080604052...). This is done to optimize space, and is the code that actually executes on the blockchain.
The problem? You can view the bytecode on a blockchain explorer, but understanding what it does is another story. Without special tools to convert bytecode to human-readable code, there's no knowing what the code does.

This creates a trust problem. A shady developer could show you clean, safe-looking source code but then deploy completely different code to the chain. Without verification, you have no way to confirm they match.
What Verified Contracts Look Like
When a contract is verified on a block explorer like Blockscout, you'll see a green checkmark next to the contract address. Click into the contract details, and you'll find tabs showing the original source code, the compiler version used, and constructor arguments.
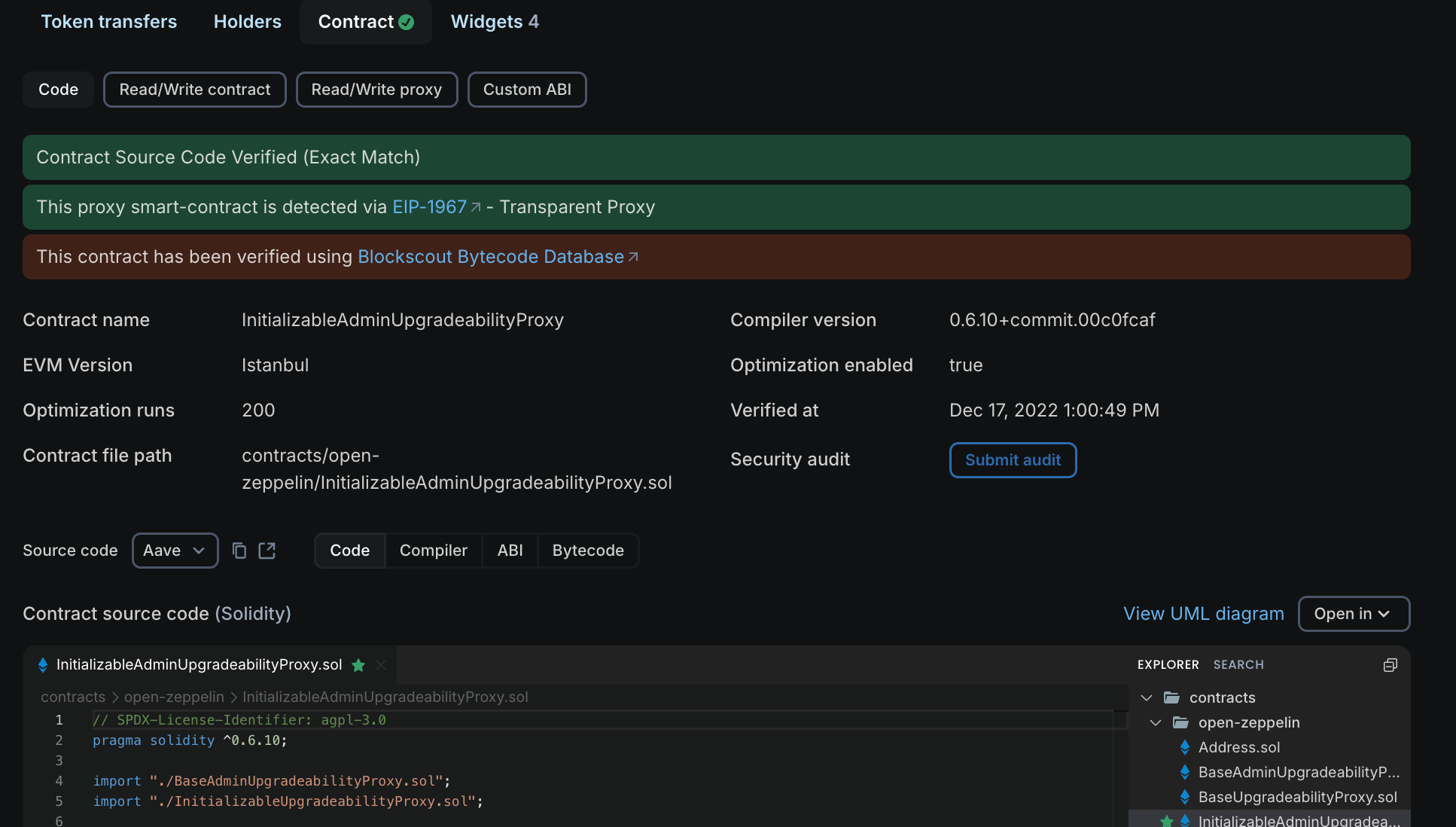
Verified contracts display their source code in full. You can read through every function, see what permissions exist, check how funds can be withdrawn, and review any admin controls. You can analyze for red flags and decide whether or not to trust the code.
More importantly, verification proves that the source code, when compiled with the specified settings, produces exactly the bytecode deployed on-chain. This proof means you can trust that what you're reading matches what will execute.
Blockscout also shows additional verification details. You'll see which compiler version was used, any optimization settings, the date of verification, and even the ability to submit a security audit.
The Verification Process
Verification works through a strict matching process. A developer submits their source code, compiler version, and compilation settings to a verification service like Blockscout's contract verifier or Sourcify. The service then compiles this code with those exact settings and compares the resulting bytecode to what's deployed onchain.
If the bytecode matches perfectly, the contract is marked as verified. The source code gets stored and displayed publicly. From that point on, anyone visiting the contract can read and interact with the original code.
Verifier Alliance: Building Cross-Platform Trust
The blockchain space has dozens of different explorers and verification services. This fragmentation created a problem: developers had to verify their contracts separately on different platforms. Users might see a contract verified on one explorer but not another, and this leads to transparency issues.
The Verifier Alliance was formed to solve this problem. This collaborative initiative includes Blockscout, Sourcify, Routescan and other major verification services working together to create a public, open and shared database of verified contracts.
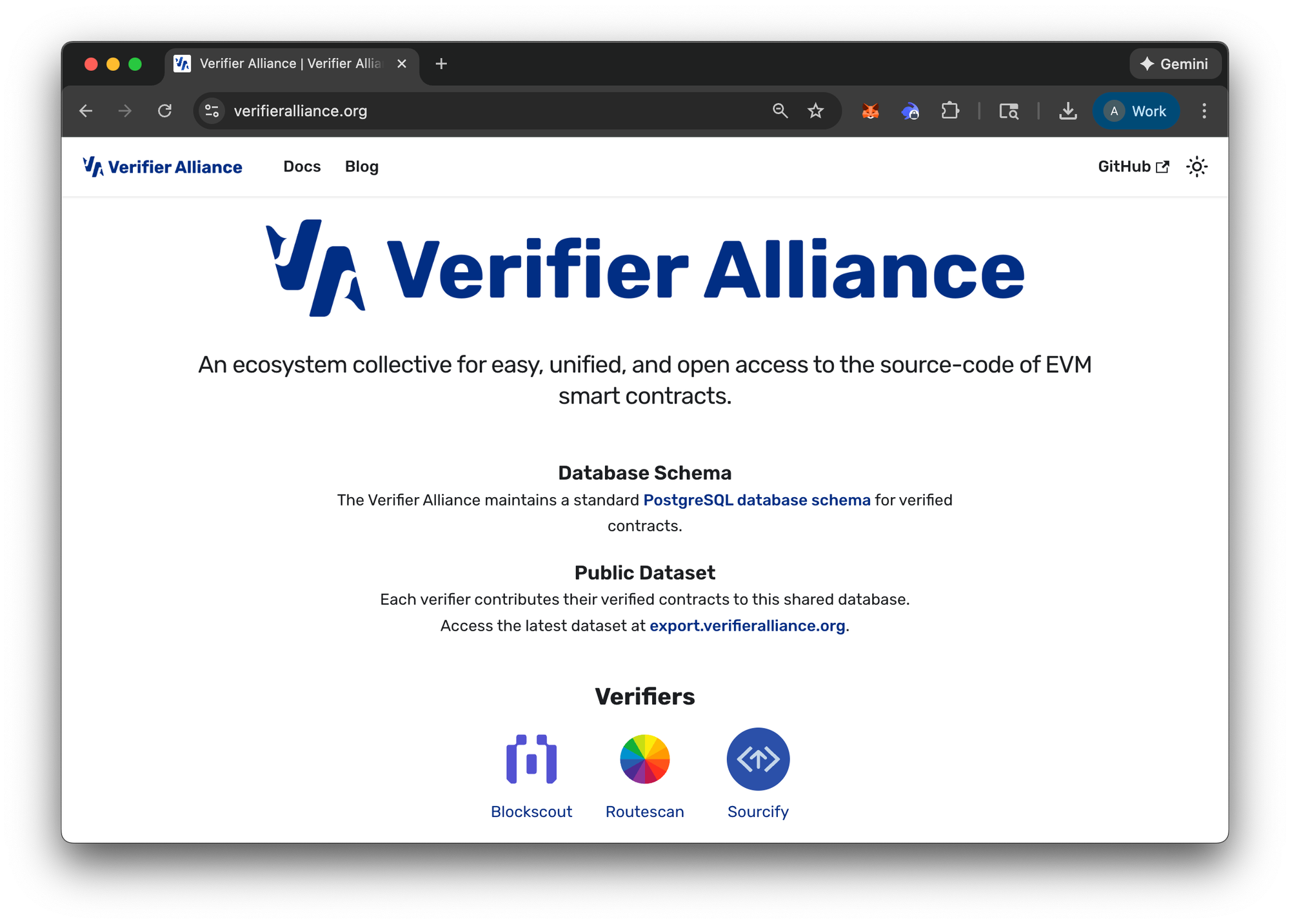
When a contract gets verified through any alliance member, that verification data becomes available to the general public and is shared amongst participating platforms.
A contract verified on Blockscout automatically shows as verified on other alliance platforms. This eliminates duplicate work for developers and provides consistent verification status across the ecosystem.
The alliance maintains a shared repository of verified contract source code and metadata. Anyone can pull from this repository to display verification information without requiring separate submissions. This standardization improves security by ensuring verification quality across platforms.
For users, the Verifier Alliance means more reliable verification status. You're less likely to encounter a contract that appears verified on one explorer but unverified on another. The collaborative approach also encourages better verification practices across the industry.
The Risk of Unverified Contracts
Interacting with an unverified contract is like using software where you can't see the code. You're trusting the developer completely, with no way to verify their claims about what the contract does.
Unverified contracts might be perfectly safe, but the lack of verification creates unnecessary risk. Malicious actors often deploy unverified contracts because they don't want users reading the code.
For example, a fake token contract might appear legitimate on the surface but include a hidden function that allows the creator to transfer tokens out of any holder's wallet. Or it might have code that blocks you from selling once you've bought in. These tricks only work when the code stays hidden.
Of course legitimate projects sometimes launch unverified. They might plan to verify later but want to test functionality first. However, users should treat unverified contracts with extreme caution until verification happens.
The absence of verification alone isn't proof of malicious intent, but it removes your ability to make informed decisions. Smart contract interaction carries enough risk even with full transparency. Adding opacity to the equation multiplies that risk substantially.
Quick Security Checklist
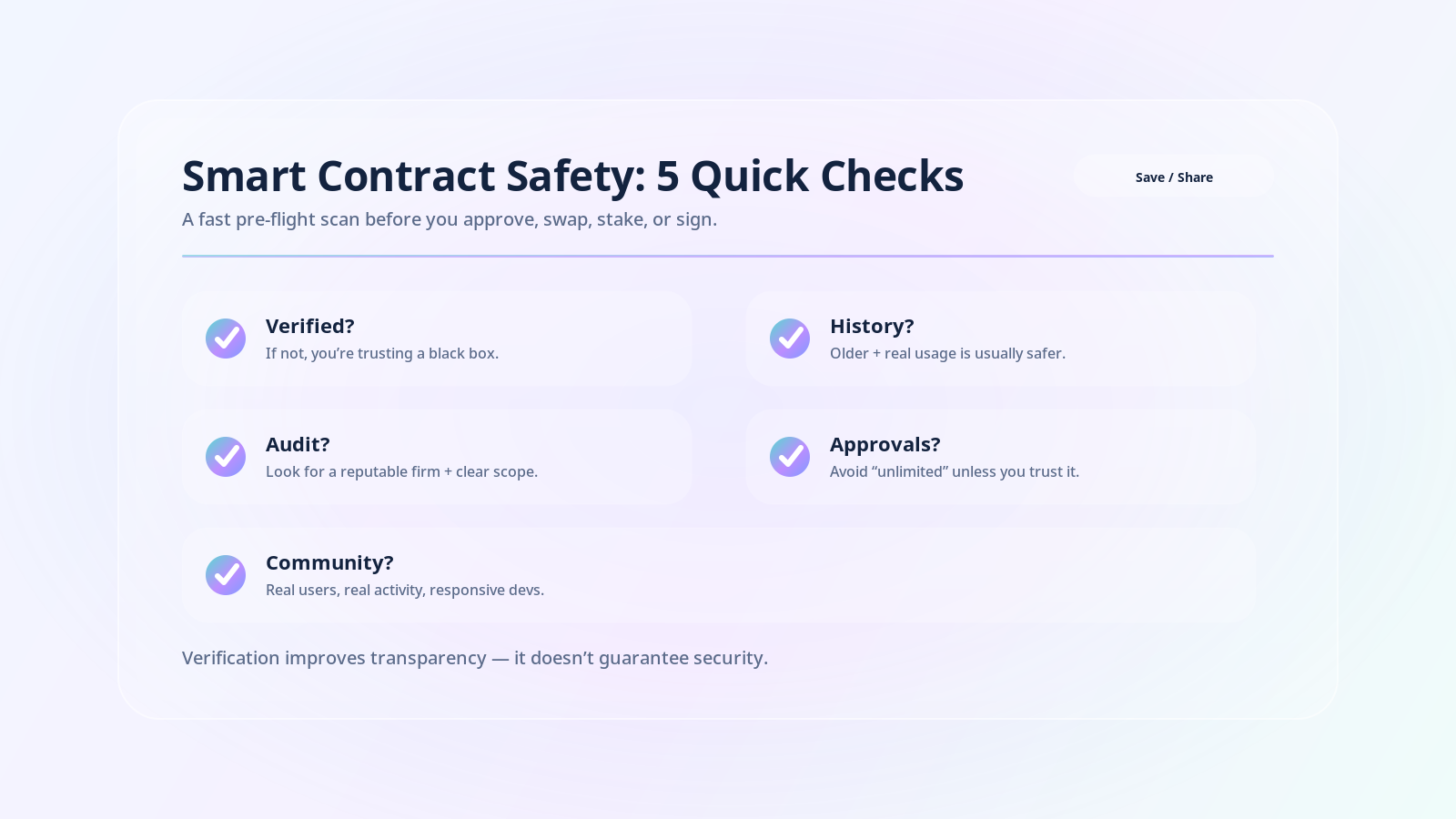
Before interacting with any smart contract, check these five things:
1. Is it verified? Look for the green checkmark on the contract page. No checkmark means you can't see the code. If it's not verified, consider avoiding it entirely unless you have a compelling reason to trust it.
2. How long has it been active? Check the deployment date and transaction history. A contract that's been running for months with thousands of successful transactions is generally safer than one deployed yesterday.
3. Can you find an audit report? Search for the project name plus "audit" to see if a reputable security firm has reviewed the code. Firms like Trail of Bits, OpenZeppelin, and Consensys Diligence publish their findings publicly.
4. What do the token approvals allow? When you approve a contract to spend your tokens, you're giving it permission to access your wallet. Check if you're approving a specific amount or unlimited access. Unlimited approvals are convenient but risky.
5. Does the project have a real community? Look for active communication channels, responsive developers, and real users discussing the project. Scams often have fake followers, generic comments, or no real engagement.
Common Warning Signs in Contract Code
Even with verification, certain code patterns deserve extra attention. You don't need to be a programmer to ask questions about these features.
Upgrade capabilities: Some contracts can be upgraded by administrators after deployment. This is done through proxy contracts that point to implementation contracts. An admin could potentially upgrade to malicious code after you've already approved the contract. Look for information about who controls upgrades and whether there are delays (timelocks) or multi-signature requirements that prevent instant changes.
Admin privileges: Check what special powers the contract owner has. Can they pause the contract? Change important parameters? Withdraw funds? These controls aren't always bad, but you should understand them. A contract where the owner can freeze your tokens or change the rules at will poses different risks than one with no admin functions.
Token minting: If the contract involves tokens, check who can create new ones. Unlimited minting by a single address can dilute your holdings or manipulate prices. Well-designed token contracts have clear limits on minting or require community governance for new issuance.
Smart Contract Security Research
The cryptocurrency industry has lost over $50 billion to exploits and hacks since tracking began. Understanding what makes contracts secure requires looking at real-world attack patterns.
Ethereum's new Trillion Dollar Security dashboard maintains detailed research on smart contract vulnerabilities and security best practices. Their analysis covers common exploit patterns that have cost users billions: reentrancy attacks (where a contract gets called repeatedly before finishing its first execution), access control failures (where anyone can call functions meant for admins only), and oracle manipulation (where attackers feed false price data to contracts).
Verification alone doesn't guarantee security. A contract can be verified but still contain vulnerabilities.
Code audits from reputable security firms provide additional assurance, but even audited contracts have been exploited. No security measure is perfect, which is why multiple layers of checking matter.
Users should combine verification checking with basic security awareness. Even without programming knowledge, you can learn to recognize suspicious patterns and ask the right questions before risking your assets.
Verification on Blockscout
Blockscout supports multiple verification methods to accommodate different development workflows. Standard verification works for most contracts, requiring you to submit source code, compiler version, and any constructor arguments used during deployment.
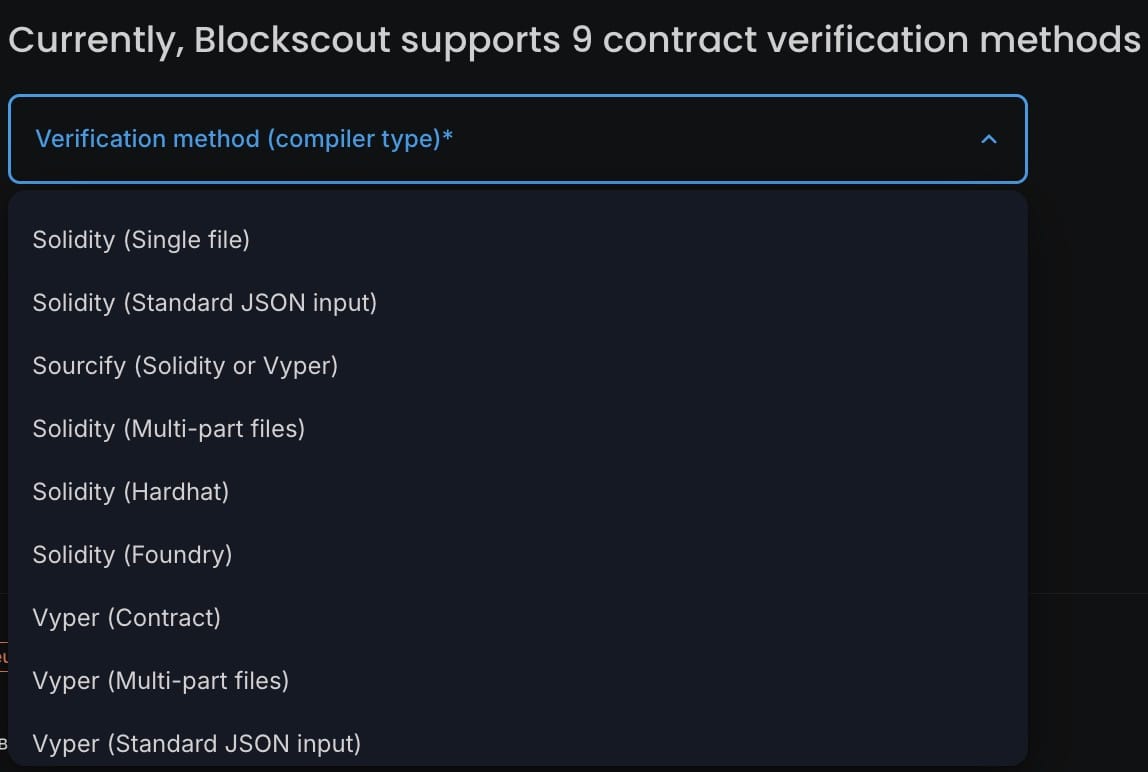
Verification status is always displayed prominently on contract pages. Beyond just showing the source code, Blockscout presents a clear interface for reading contract functions, understanding events, and tracking contract activity.
Making Verification a Habit
Contract verification represents one layer of blockchain transparency. Combined with open-source block explorers like Blockscout, public transaction history, and collaborative initiatives like the Verifier Alliance, it creates an ecosystem where users can verify what's happening with their assets.
This transparency separates blockchain from traditional finance, where you trust intermediaries without seeing the actual code handling your money. With smart contracts, you can verify the rules before agreeing to them.
But transparency only helps if people use it. Checking verification status takes seconds and can save you from costly mistakes. The next time you plan to swap tokens, stake assets, or connect your wallet to a new protocol, pull up the contract on Blockscout and run through the quick checklist above for a little extra peace of mind!


