How To Not Lose $50 Million: Address Poisoning Antidotes
Learn how address poisoning scams work and why users fall for them. Discover how block explorers like Blockscout help detect lookalike addresses and prevent costly mistakes.

In December 2025, one of the largest single exploit events reported involved an address poisoning attack that siphoned off $50 million in USDT after a victim mistakenly sent funds to a scammer’s address that looked nearly identical to their intended destination. The attack was buried within routine wallet activity until it was too late.
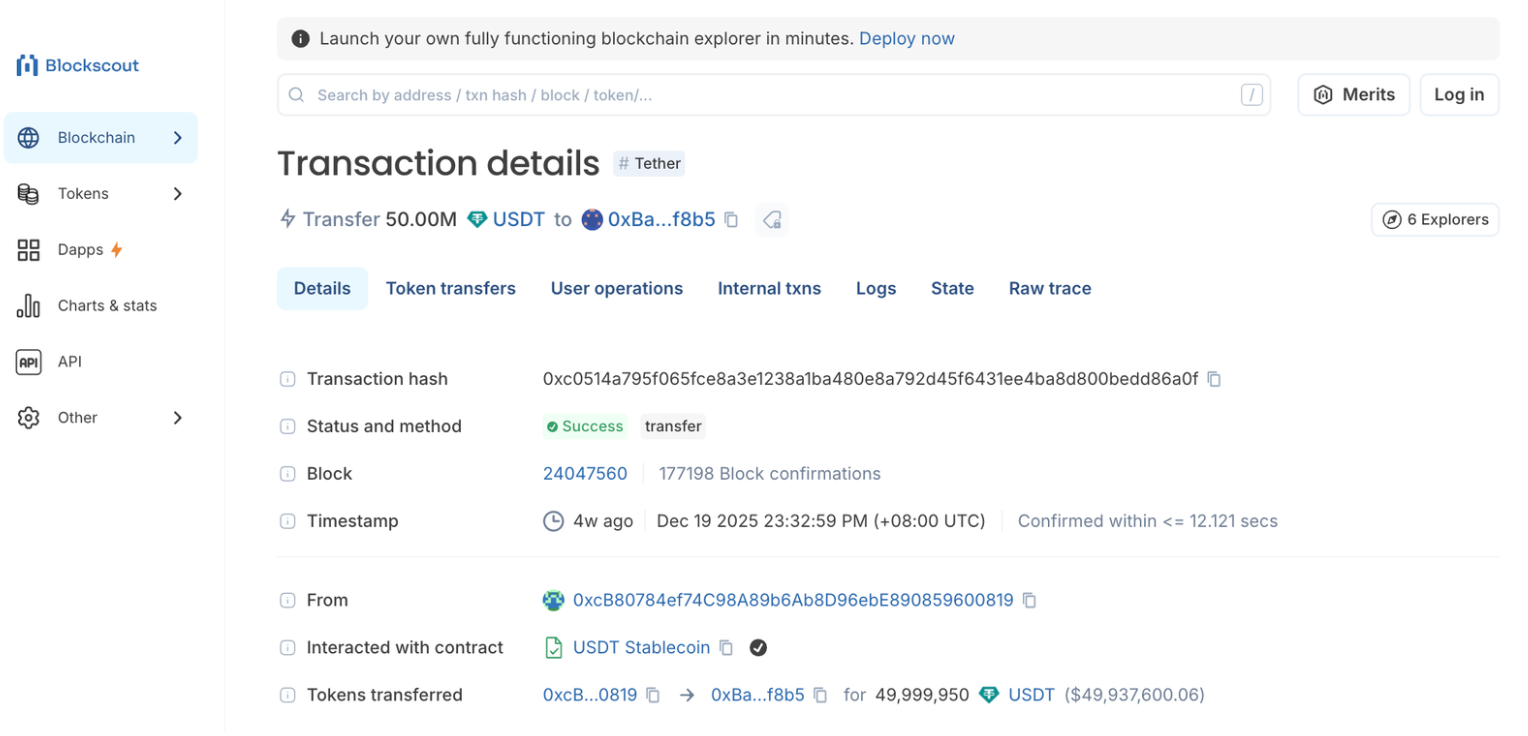
This isn’t a cunning phishing link or some complicated exploit on a smart contract. Address poisoning works because it plays on how people use crypto tools every day.
How Address Poisoning Works
At its core, an address poisoning attack is a social engineering exploitation of address similarity and transaction history.
The attacker’s goal is simple: get a malicious address to appear in your wallet’s recent activity so that it looks trustworthy the next time you send funds.
Here’s the sequence in clear terms:
1: Create Lookalike EOA
Attackers use software to generate wallet addresses that are near-matches to an address a target has previously used.
For example, the attack address might share the same first few and last few hex characters as your trusted counterparty. People tend to scan the first and last characters of long strings and gloss over the middle. This is where the deception lives.
2: “Poisoning” the History with Dust
The attacker sends a tiny or zero-value transfer (dust) from this lookalike address to your wallet. Because most wallets and explorers list transactions chronologically without filtering by value or context, this fake transaction appears alongside legitimate history.
3: Copy-Paste Trap
Next time you initiate a transfer, you reach for your recent transaction list, copy what appears to be a trusted address, and paste it into the recipient field. But it isn’t the one you think it is.
4: Send to scammer
Once you broadcast that transaction, blockchain irreversibility guarantees there’s no refund. Funds go straight to the scammer’s wallet.
The attack doesn’t require hacking private keys, bypassing signatures, or tricking wallets into revealing secrets. It depends on users trusting what they see.
Why Users Fall for It
This attack strategy succeeds for two related reasons:
Human Interface Limitations
The classic 0x wallet addresses are long hexadecimal strings. Most interfaces truncate them, showing only the first and last few characters, because only Rain Man would memorize a full wallet address. That truncation is convenient, but it’s exactly what makes lookalike addresses effective.
Reliance on Transaction History as Source of Truth
Many users treat past transactions as their address book. That behavior might be rational to some, but the problem is that transaction history doesn’t have any built-in integrity checks. It just shows entries pulled from onchain activity.
When an attacker poisons that history with a near-match, it feels familiar, even though it’s controlled by an adversary.
How Block Explorers Help Expose Address Poisoning
Block explorers don’t prevent address poisoning directly, but they are effective tools for breaking the illusion of familiarity that makes the attack work.
With the right interpretation and tooling, they can directly limit the chances of the attack working.
Check the full address
Before sending funds, pasting the destination address into Blockscout and opening the full address page lets you verify the complete string and it's associated onchain activities, not just the characters your wallet displays.
This alone defeats many poisoning attempts.
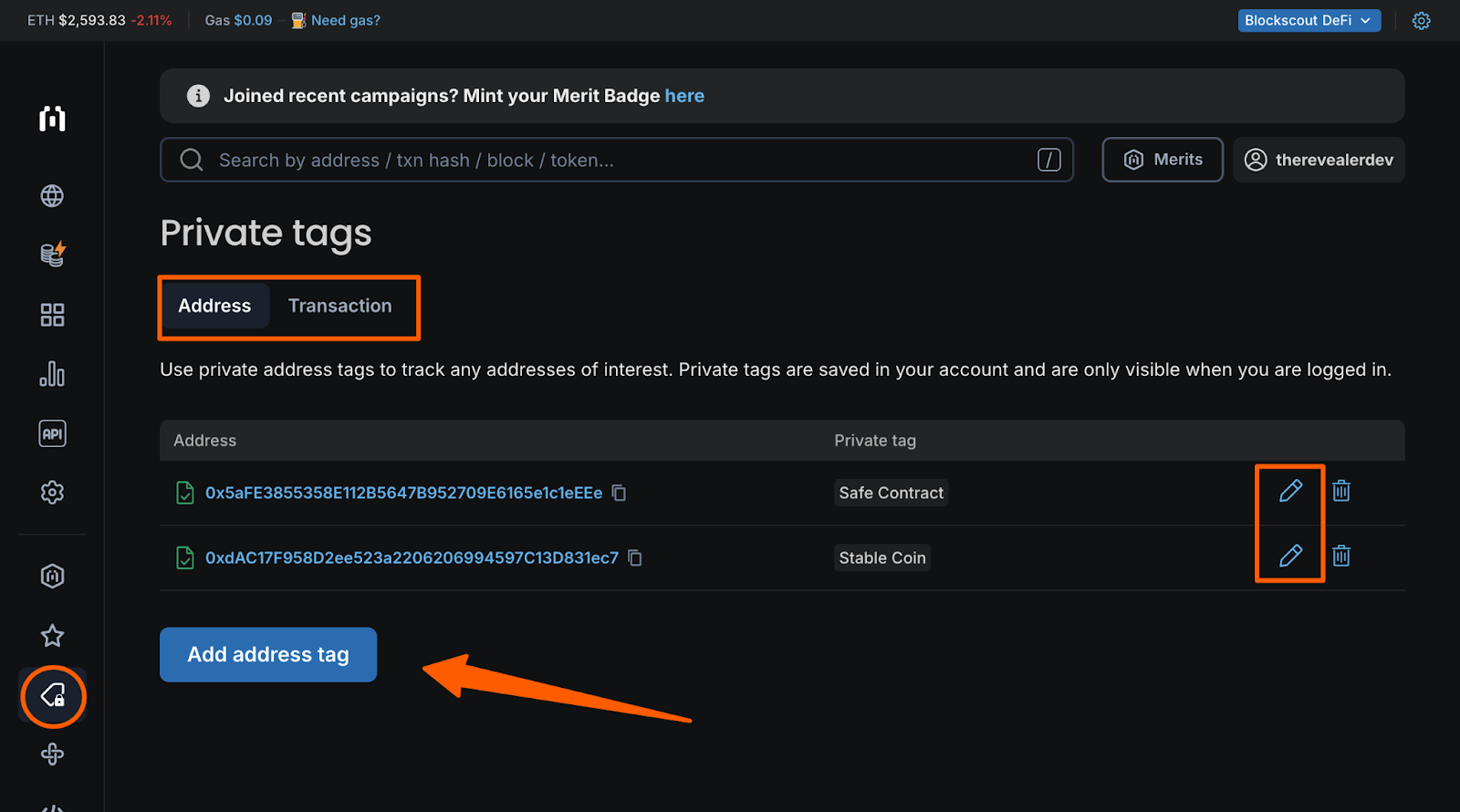
Add private tags to trusted addresses
When you connect your wallet to Blockscout and create an account, you can add private tags to addresses that you trust. This changes what you see in your transaction history:
- Tagged addresses represent intentional relationships
- Un-tagged addresses stand out because they lack context
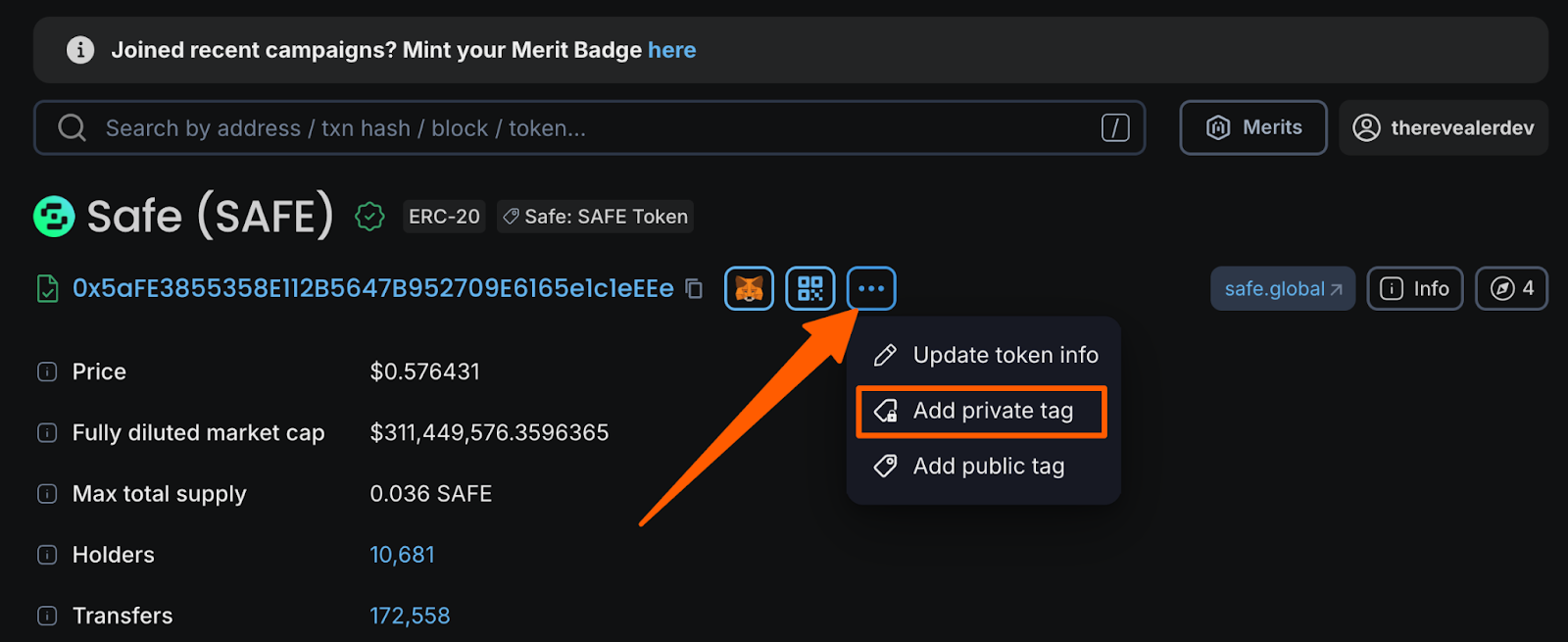
Instead of copying from recent transactions, users can copy from their own tagged addresses, which attackers cannot modify or spoof. This way, tags function as a persistent memory layer that poisoning attacks cannot penetrate.
Inspect EOA behavior
On an explorer, you can see how an address behaves over time.
Poisoned addresses often share patterns:
- minimal transaction history
- dust-level outbound transfers
- no meaningful inbound value
- no interaction with known contracts
Legitimate counterparties usually show repeated activity, varied transaction sizes, and clear interaction history.
You can also tag these poisoned addresses that seem to target you specifically, to make sure they are clearly marked as SCAM.
Additionally, some of the Widgets on EOA pages that Blockscout shows also help to identify scam wallets. For example, the scam wallet in the $50M heist has a Risk Score of 100.
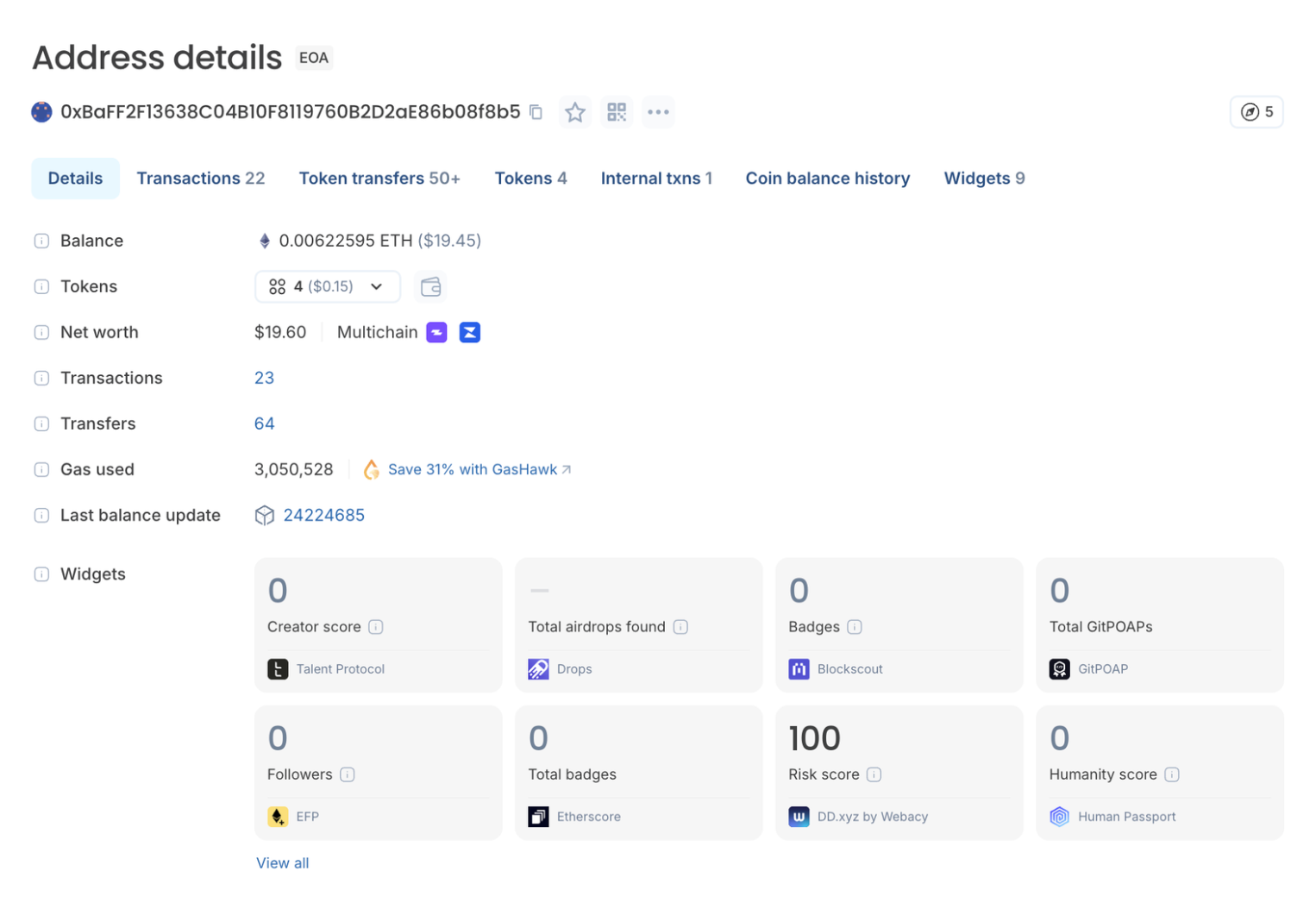
Using Blockscout as a second confirmation step slows down the exact behavior address poisoning relies on: fast copy-paste decisions made from partial information.
That friction is now a feature.
Use multichain search to expand your threat model
Address poisoning is frequently automated and multichain.
Using Blockscout’s multichain search, users can search a suspicious address across multiple networks to see whether it appears elsewhere.
This matters because:
- attackers often reuse address generation logic
- poisoned addresses may already be active on other chains
- a clean-looking address on one network may show clear scam behavior on another
Once identified, users can privately tag that address across chains, building their own cross-chain blacklist.
Make 0x addresses simple with domain names
Address poisoning works because users are forced to interact with long hexadecimal strings. Onchain naming systems like InfinityName, ZNS, and ENS, reduce that risk by replacing raw addresses with human-readable identifiers.
This works because domain names don’t rely on partial visual matching, there’s no “middle section” to silently swap, and the name itself is what users verify, not a fragment of an address.
You still need to make sure you don’t fall for simple tricks like swapping Allstar.blue with AIIstar.blue (spot the difference), but that should be easier to catch compared to 0x trickery.
Block explorers reinforce this by making name resolution easily auditable. On an explorer, users can:
- confirm which address a name currently resolves to
- see when that mapping was last updated
- inspect the resolved address before sending funds
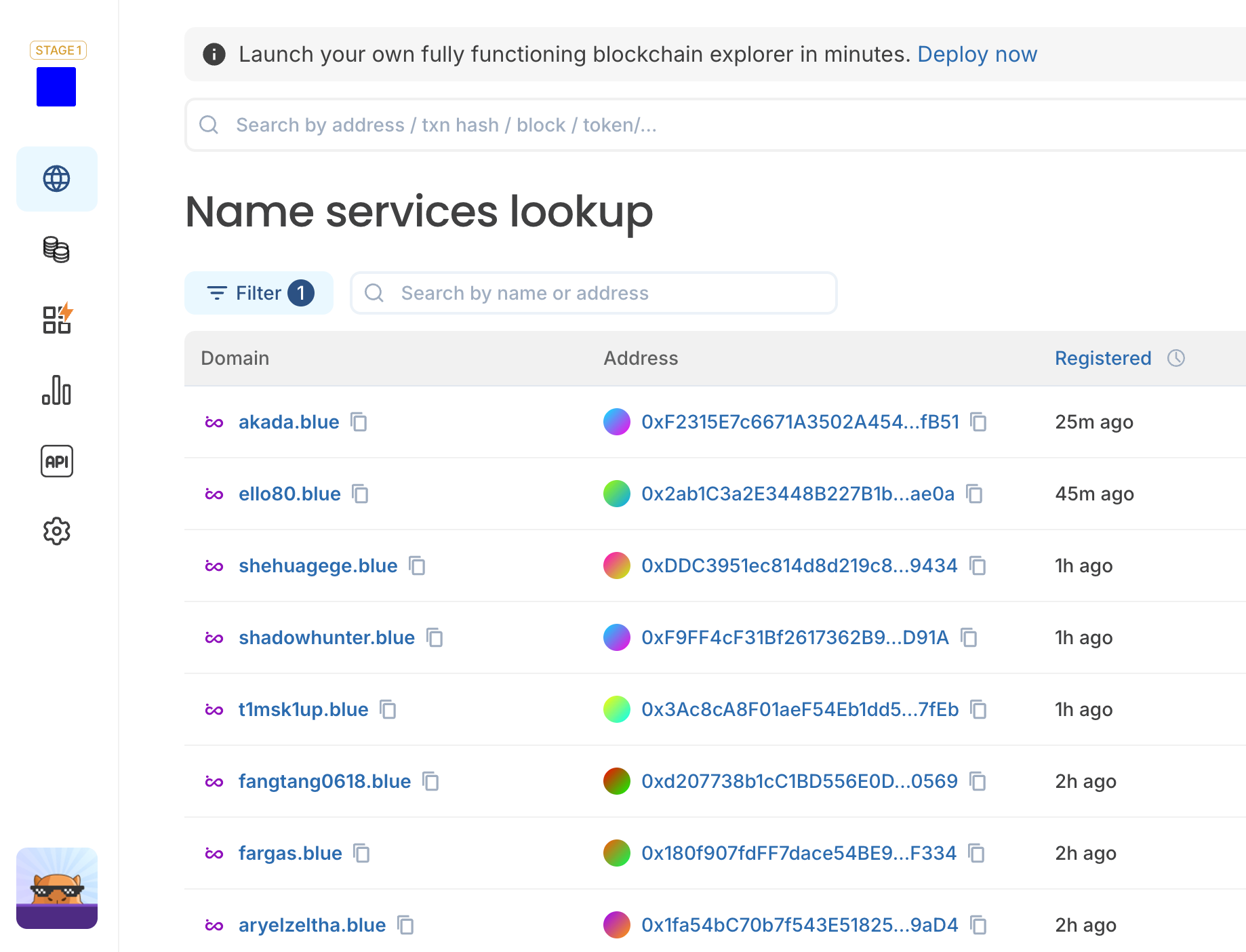
Using names doesn’t eliminate all risk, but it significantly reduces dependence on transaction history and makes address poisoning harder to execute undetected.
Practical Habits Beyond Block Explorers
Explorers are powerful, but they work best alongside good operational habits.
- Never copy addresses from transaction history
- Never, ever, copy addresses from transaction history
- Always verify the full address for high-value transfers
- Save trusted counterparties in a dedicated address book when possible
- Prefer hardware wallets that display the full destination address on-device
- Rotate addresses when possible to reduce exposure
None of these are complex. They just require intentionality. And that’s often all it takes.
Don’t Forget About Permissions
Even careful users accumulate risk over time through old and forgotten token and dapp approvals. Regularly reviewing and revoking unnecessary approvals with Revokescout reduces that risk.
It limits what an attacker or malicious contract can do to your assets right now, even though you've interacted with the compromised smart contract in the past.
🛡️ Security always comes first
— Blockscout 🔭 (@blockscout) January 9, 2026
We’ve been seeing more exploits recently, and there’s a simple habit that can significantly reduce your risk: clean up your token approvals with Revokescout
Check and revoke now 👇https://t.co/rw4oToo9At
--
Tell me more 🧵
When you use dapps,… pic.twitter.com/GHrsmT9i0Z
Address safety and permission hygiene solve different problems, but together they significantly improve onchain security.

